Digital Safeguards Communications

Data leaves your device and enters the network when you
- explicitly send or receive documents or messages to your clients, vendors or others
- enter customer data on a website (e.g. using an online service to store or process client paperwork)
Data is at risk whenever it leaves your device. Data traveling over a network can often be read (snooped, eavesdropped) by unauthorized parties.
For instance, someone parked near your location can intercept and read all data sent over your WiFi network, even without connecting to your network, using just a laptop and some free software. Even data on your wired network can be intercepted using relatively cheap and inconspicuous devices attached to network cables, possibly outside your office or facility.
The three most important network security holes to close are the following:
- Encrypt your WiFi network
- Use encrypted email or document portals for communicating sensitive information
- Do not enter passwords or sensitive data on websites that do not use HTTPS
The following sections explain each of these aspects.
Encrypt your WiFi network
The best current standard for encryption for WiFi networks is WPA2. To ensure you are using it, logon to your wireless router’s management page and under WiFi settings make sure you are using WPA2 (it may be labelled WPA2-PSK or WPA2-Personal on your WiFi router). When WPA2 is enabled, the data sent between your wireless devices (computers, phones) and the router is encrypted on the wireless channel. So someone eavesdropping on your network traffic, say from a car parked nearby, will only see encrypted data. (Some routers may offer the WPA2-Enterprise option as well - that is meant for an enterprise network with many computers and most people would want the help of an IT pro to set that up.).
The steps below explain this in more detail:
Connect to your router: To connect to your WiFi router’s management/settings page, you will typically visit an address such as 192.168.1.1 in your web browser from a computer connected to that router’s network. The exact address to use may be listed on a sticker attached to your router. Alternatively, in Windows, open a command prompt: press the Windows and “R” keys simultaneously, and in the little window that opens up, type “cmd”:
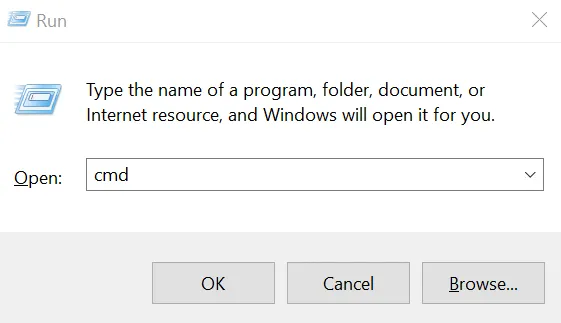
Press OK and in the command prompt that opens, type the command “ipconfig.” Press enter. In the response printed by that command, look for your network adapter that is being used, usually labelled “Ethernet adapter” or “Wireless LAN adapter…”
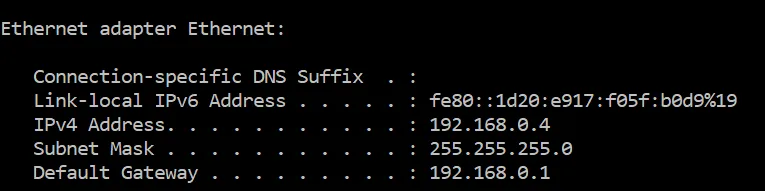
Look at the entry next to “Default Gateway” and that is the router’s network address. For instance, if the default gateway shows 192.168.0.1, then you would connect to 192.168.0.1 using your web browser.
This page will ask you to login. Typically, the username is “admin” and the password is what you have set when you set the router up. If you have not changed the password from the default setting, use the default password and change it immediately. The default password is not secret and anyone may use it to connect to your router, to effectively have complete control of your network including its security settings.
Some of the newer routers may even allow you to visit the router management page on a product specific website such as http://linksyssmartwifi.com/ for Linksys routers.
Find the wireless settings page: Once logged in, look for a menu option or link to “Wireless Network” or Wireless settings, or Wireless security. These settings may sometimes be under Router Settings or Wireless depending on your wireless router’s model and brand.
Here you will likely find a setting called security mode or something similar that has options such as WEP, WPA, WPA2-PSK, or WPA2-Personal. If WPA2 (or WPA2-Personal, WPA2-PSK) is not already selected, select that. You will also be required to set up a password for your WiFi network. Do not use a password that you might be using for other websites since this password may have to be shared with everyone who needs to connect a device to your WiFi network, such as your staff or family members.
After this setting is changed, any devices, such as your computers or phones using the WiFi network will need to reconnect to the WiFi network, using the network password you set above.
Encrypted Email or Document Portals
You may have noticed that banks never send you statements over email. That is because email is not secure. Even if your computer’s connection to the mail service is secure, there is no guarantee as to what happens when the email leaves your email server to start its journey towards the recipient’s email server and eventually their device.
Up to 20% of all emails are routinely attacked, say researchers at Google, University of Michigan and University of Illinois Urbana Champaign, after studying 700,000 email servers.
Major email providers (Hotmail, Yahoo, Gmail, AOL) and millions of other email domains “offer no protection against active adversaries” who could observe or inject data between an email server and the Internet, say Prof Alex Snoeren and his fellow computer scientists at University of California San Diego, based on their measurements of current email services.
The fact is that security configurations vary greatly across email servers and data may be sent unencrypted even between two email servers that both support encryption, if their encryption settings are incompatible.
The best defense is to use a secure document portal. Encyro provides a free document portal that encrypts your data both on the wire and when stored, using secure bank-level encryption technologies, and only stores data in security certified data centers. You simply send a message or attachment like you would using email and Encyro automatically creates a document portal for you and your client.
-
In your portal, you can track all messages and documents organized by client folders. They remained stored securely and backed up offsite with encryption.
-
Your clients are not required to create an Encyro account and simply access the document securely using a secure link sent to their email. They may of course create a free account if they wish, and they too get continued access to the secure documents and messages, they receive from you, and optionally send to others.
-
Unlike other portals, Encyro allows your clients to forward documents to others (e.g. they may send their previous year tax return to their loan officer for a refinancing application). This helps your clients stick with you, since your portal becomes part of a rich network of multiple services that they use.
You can try how easy it is for your clients to receive documents you send using Encyro, using the free trial offer below.

Use HTTPS
Never enter passwords or any sensitive information such as client data on websites that do not use HTTPS. HTTPS encrypts the data between your computer and the website. So, as the data travels across the Internet across many types of network equipment, someone eavesdropping on your data will only see encrypted information and will not be able to steal your actual data.
Websites that use HTTPS will show a web address that starts with https:// instead of http:// (note that S at the end). Your web-browser will show you when a website uses HTTPS.
For instance, Chrome shows a “green lock icon” on the left in the browser web-address window:

Next to the green lock icon, you might either see the word Secure or the name of the company that owns the website.
Internet Explorer shows a gray lock icon on the right:

Microsoft Edge shows a gray or green lock icon on the left:
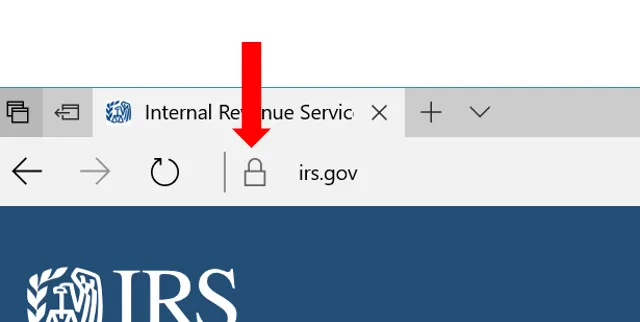
Web-browsers on the phones similarly show a lock icon as well. Safari on iPhones for instance shows a black lock icon.
Most legit businesses that ask for any sensitive information, including a password to login, do use HTTPS. New browsers will even show you a warning when a website appears to be asking for your password on an insecure connection.
If a vendor service that you use asks for your password or any sensitive information on a website that is not HTTPS protected, it usually demonstrates lack of security awareness or concern for your data. It could even mean the website you are visiting is not the intended one but a fake. It is best to stay away from such websites.
Even if your WiFi network is encrypted, that encryption ends the moment the data from your computer or device reaches the router. From the router to its destination on the Internet, the data is NOT encrypted by WPA2. Also, WPA2 does not encrypt the data on the wired connections. Wired connections are harder to eavesdrop on since they require installing a “bug” device on the network cables but such devices are cheap and readily available.
That is why using HTTPS is very important - to make sure the data remains encrypted all the way to its destination.
Use the digital safeguards: data communications worksheet in this free data security template to verify that the steps discussed in this section are taken care of.