5 Ways to Encrypt Email For Your Business

Choosing the wrong email encryption could shoo away clients by introducing unnecessary friction. And you may be paying for something that is not as good when the best solution is actually free.
Each encryption service possesses different pros and cons, suited to different situations or businesses. This article will help you make the best decision for your business and professional use.
Here are the different ways you can encrypt email, as of this writing:
- Encryption in Transit (using TLS)
- Enterprise Email Encryption
- DIY Email Encryption
- Secure Webmail
- Encyro
We evaluate each of these for ease of use and security for business use.
(If you want to compare encrypted webmail only, go to an up to date comparison of best encrypted email for small business.)
Why Encrypt Business Email?
Sending sensitive information over email is still not safe. Up to 20% of all emails are routinely attacked, say researchers at Google, University of Michigan and University of Illinois Urbana Champaign, after studying 700,000 email servers.
“Sixty percent of small businesses close down after a data breach”
- U.S. SEC
Protection is a Must-Have
Obviously, businesses want to use email encryption rather than dealing with the consequences of data breaches. All businesses are required by law to report data breaches to not only the state but also their clients. And no one wants to end up on their state’s public list of breached businesses. Or pay the state mandated penalties, up to $250,000 in some states.
Sixty percent of small businesses close down after a data breach, according to this report by the US Securities and Exchange Commission. Even if your business does survive, you still have to deal with the loss of business reputation and goodwill. Clients do not always understand whose fault it is. And even when they think it is not your negligence, they may just play it safe by staying away from your systems. The incidence of consumer identity theft and related crimes has been rising very rapidly (see data from US Department of Justice and reports by the Federal Trade Commission).
As a result, regulatory bodies such as the Consumer Financial Protection Bureau (CFPB) have now been charged with the responsibility to enforce data privacy laws. The primary law that affects registered investment advisors, real estate settlement agents, lenders, collection agents, and other small businesses is the Privacy of Consumer Financial Information Rule of the Gramm-Leach-Bliley Act. Fortunately, encrypted data, even if stolen, is not considered a breach in most situations.
“Identity theft has become widespread, affecting nearly 17 million Americans”
Growth Opportunity
Furthermore, professionals have a growing desire to protect customer data. Their customers are growing increasingly aware of email associated risks. They know identity theft has become widespread, affecting nearly 17 million Americans. It is no longer limited to minor credit card fraud but now includes more serious crimes such as house stealing even when the owner is living in the house. So when you as a professional show extra care for customers’ information, it proves:
- You care for your clients’ data. This is huge for earning greater trust.
- You have sophisticated business processes in place, that only come with experience and expertise. So you stand out from the newbies and part-timers.
How To Compare Email Encryption Methods
Multiple options to secure email differ in their security features and ease of use. The reason being that each one was designed for a different purpose. Some were designed for companies that want to enforce security on their employees’ email usage, minimizing employee error. Such systems offer rich security policy configurations. Although an IT expert and the overhead they would incur would likely be necessary in setting those policies up.
Others were designed for compliance where both the sender and receiver are required by law to encrypt in a certain way. Ease of use or actual protection against modern attacks was not a concern. Yet others were built for freedom fighters wanting to avoid government surveillance but willing to put up with jumping through hoops to get to their messages.
We want to select an email encryption option that’s best for business. Especially for independent professionals and small businesses, who do not have a dedicated IT department. The solution of choice will be the one that offers the best security to protect the business and its customers, while at the same time ensuring a smooth customer experience.
Here is what we should evaluate for each email encryption option:
Security
- Breach In transit: Can the email be read by an attacker while travelling over the network?
- Breach when stored on a server: Will theft or unauthorized access to a storage device, such as a hard disk or a computer at your, or your receiver’s email server, or any intermediate email relay cause your data to be leaked.
- Breach when stored on devices (phone, laptop, desktop): Will theft, loss or unauthorized access to your device cause emails to be leaked?
Ease of use (for you and your clients)
- Set up: How easy is it for you to install, create an account or otherwise get started with using it?
- Daily Use: How easy is to send and receive emails after correctly setup?
- Easy for clients to receive: How easy is it for your clients to open your encrypted messages, if they do not have an account with the same encryption service or use the same email product as you?
- Easy for clients to send: How easy is it for your clients to send you an encrypted message (or document)? Do they need to create their own encrypted email account or install an encryption product?

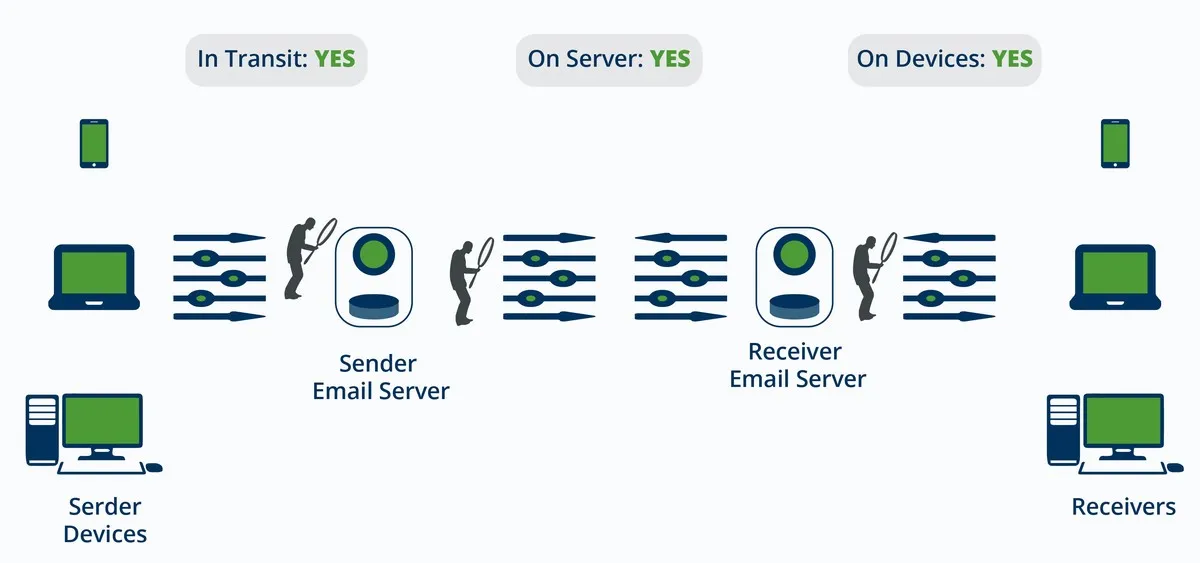
1. Encryption in Transit (using TLS)
Encryption in transit means that the email data is encrypted while it travels from one email server to another. This approach is based on a mail server configuration known as Transport Layer Security (TLS). It is being promoted by major email providers, such as Gmail, Hotmail and others.
It protects against eavesdropping or snooping, a security attack where data traveling over a network cable or wireless connection is intercepted by the attacker. Such attacks are easy these days and require less than $50 of tiny hardware modules that can be attached in a few minutes to a network cable when the attacker has access to such a cable from a network service provider, such as in street-side communication equipment boxes, business offices, or other locations.
Ease of Use: Super-easy
Setup: You need not do anything extra to setup. As long as your email provider uses it, you get this benefit automatically. There is usually nothing else you need to do. Only configuration you should verify is that SSL is used for the connection from your device to the email server.
If you connect to your email using a web browser, make sure you use HTTPS (not HTTP) at the start of the URL. In most cases this is automatically ensured by the webmail service.
If you check your email from an app, such as Outlook on a desktop or the iPhone Mail app on the phone, make sure that Secure Socket Layer (SSL) is enabled. SSL secures the connection from your device to the email server, much like TLS secures the connections between email servers.
On iPhone for instance, go to Settings > Mail > Accounts. Then select the account you are checking. Tap that account and within that you may have to tap the option ‘Account’ again to get to a screen that offers ‘SMTP’ as one of the options. Now tap SMTP and select the mail server. The options here may vary somewhat based on the type of mail server. What you are looking for is an option called SSL. “Use SSL” or SSL should be ON. Sometimes this switch may be faded green to indicate you are not allowed to turn it off - that’s a good thing!
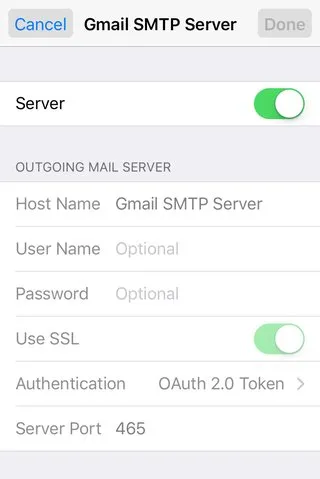
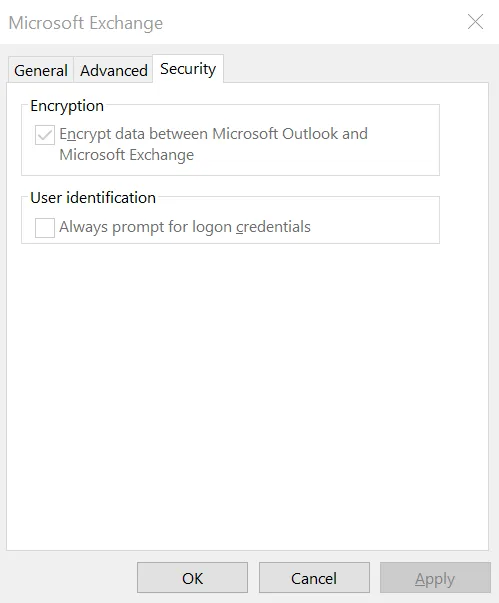
In Outlook for desktop PCs, go to File > Account Settings. Select the account and then Change > More Settings > Security. Here you should see a setting that indicates “Encrypt data between Microsoft Outlook and [your mail server].” The exact words may vary based on your Outlook version and email server. This setting should be enabled.
Daily use: You use it just as your regular email without encryption.
Easy for clients to receive: Your clients can open your messages easily. TLS will be silently disabled if the recipient does not support it. Ease of use prevails over security here.
Easy for clients to send to you: Your clients email you normally. TLS only kicks in if their and your servers support it and are configured in a compatible manner. Otherwise the message will travel without encryption, but it will travel.
Let us summarize the ease of use rating using numbers to compare easily with other choices at the end.
| Ease of Use | Rating | Score |
|---|---|---|
| Setup | 5 | |
| Daily Use | 5 | |
| Client Receive | 5 | |
| Client Send | 5 | |
| Overall | 5 |
How Secure: Better than not having any security.
In Transit? Yes. The primary protection is for the time the email data is traveling over the network, but only if traveling between correctly configured mail servers. The research mentioned above found that only 35% of the 700,000 mail servers they studied were actually configured for encryption. And that is not surprising. According to Johanna Amann, PhD, working at University of California Berkeley, “most of our communication is poorly secured” because “secure configuration is not straight-forward and many combinations of encryption and authentication mechanisms lead to insecure deployments” based on research with her co-investigators from University of Sydney and Technical University of Munich, presented at the Network and Distributed System Security Symposium 2016.
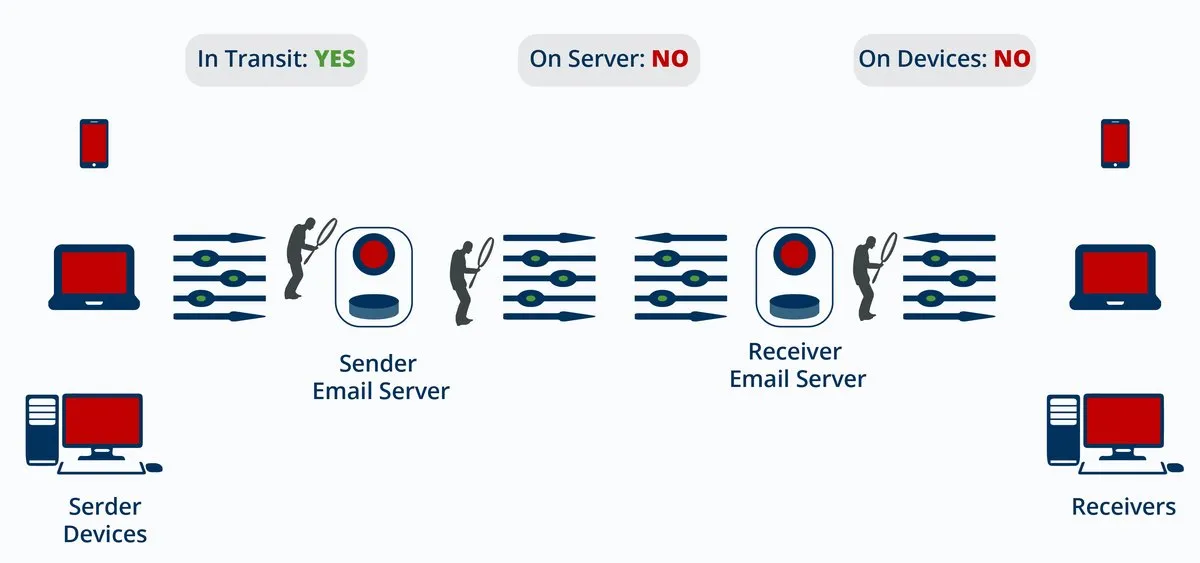
On Server? No. TLS does not encrypt stored data on mail servers or any other intermediate message handling services (MHSs), message transfer agents (MTAs), or mail relays.
On Devices? No. Also, TLS does not protect the email stored on your and your recipients’ devices, such as in the inbox, sent mail, and outbox folders.
2. Enterprise Email Encryption
This type of email encryption strives to make encryption transparent for users. They can send email from an encryption enabled email client application. Outlook for example, with an encryption plugin or a custom application. The encryption product or service may be installed as software on your company’s email server. It could be an additional hardware device on your company’s network, or cloud based. They generally encrypt the message either at the sender device, such as using their email application or Outlook plugin. In other instances encryption may happen at a server within your company’s network.
These are generally aimed at larger businesses. Such systems are expensive and require extensive IT configuration for setup. They are sometimes limited to customers purchasing at least 50 or 100 employee licenses. Although, some vendors have been known to offer versions for lower volume purchases.
The big advantage here, is that using encryption is largely transparent for employees. They would access their email using a company assigned email application and continue to use their company email address. Encryption would happen behind the scenes.
A further advantage is that most enterprise email encryption products offer additional policy features. For example, to automatically encrypt certain types of emails, say, when emails seem to contain social security numbers. Policies could be set up to prevent certain types of data from being emailed outside the company. Or to store audit logs for in-depth reviews. They may also help ensure compliance with relevant regulations. Some of these products even offer tracking delivery and email opens.
These products allow you to manage your own encryption keys. A potential advantage, particularly for large corporations, is that these products allow you to manage your own encryption keys. If you choose this option, even the email encryption vendor cannot decrypt your email. Of course, you must make sure that key management and backups are correctly configured. Remember, losing your encryption keys will be tantamount to losing your email messages altogether.
Options include ZixMail, Symantec Messaging Gateway, ProofPoint, Cisco IronPort, Rmail, Virtru and also built in features in Microsoft Exchange, among many other custom solutions offered as part of data loss prevention packages.
Ease of Use: Easy for enterprise use. Difficult for smaller businesses
Setup: This is not something you would simply sign up for online. Rather, you would first request a demo and the vendor would recommend you use the correct setup based on how your existing email service is set up. Pricing may be negotiated based on your purchase volume. Then a hardware device may be shipped to you if needed and our IT staff will set it up. Alternatively, the encryption vendor may set it up for you or recommend an IT consultancy service to do it. You will likely first test with a few employees and then make it available to everyone in your organization. Newer products are making this step easier than it used to be in the past but because they must add a software component or server to your endpoint, the setup does require some work.
Daily Use: Once setup, it is easy to use. Typically the sender does not have any extra steps, though some systems may offer the options to select send without encryption or with encryption, and that’s one minor selection to make when sending. The only caveat is that, depending on the vendor you selected, you or your employees may be restricted to sending secure email only from devices directly connected your organizations network. Or only using the email application provided by the vendor. This would make it difficult to send encrypted emails from smartphones, or from laptops when outside the office. For example, Rmail does provide a mobile app for iPads though not for Android devices or the iPhone. Virtru is one of the few that does offer mobile apps for iOS and Android.
Easy For Clients To Receive: If your clients are other enterprises with the same email encryption product in use, then they will receive your encrypted email as easily as regular email. So if you serve one or a few large corporations, it is worth finding out which email encryption setup they use and get on the same one.
If your clients do not use the same encryption product, such as when you serve individual customers or other small businesses… That’s when receiving becomes more complex. In most systems, the receiver will get a link to click. What happens with the link varies. For example:
- ZixMail will force your client to create a Zix Message Center account.
- Microsoft Exchange will require the receiver to create a Microsoft account with the same email that you sent the email to. So if you sent the email to the client’s Gmail address, the recipient will need an account with the Gmail address as the Microsoft account login. Even when the client may have a different Microsoft account (Hotmail address) that maybe they do not use anymore. Alternatively, they offer the recipient to request a single use code from Microsoft over email.
- RMail requires the receiver to enter a password that either you share with them or RMail sends them in a separate email.
Easy for clients to send: Clients cannot send unless they create their own account with the encrypted email service provider. With providers that require your recipients to create an account just to read your message, that account often allows sending replies to you.
To summarize:
| Ease of Use | Rating | Score |
|---|---|---|
| Setup | 1 | |
| Daily Use | 4 | |
| Client Receive | 3 | |
| Client Send | 0 | |
| Overall | 2 |
Security: High. Two of three aspects covered.
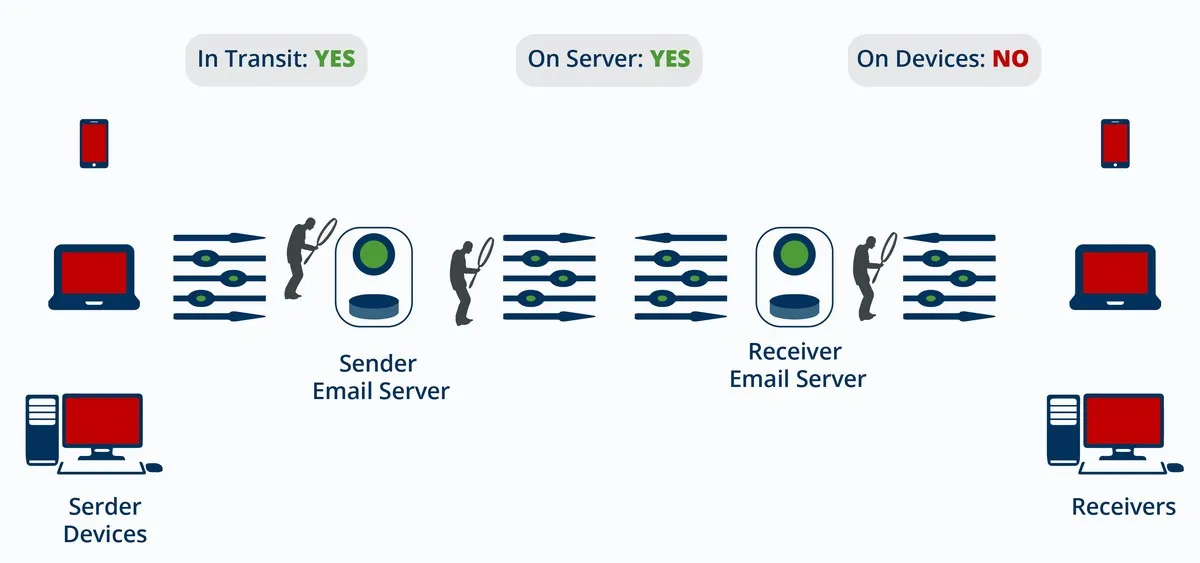
In Transit? Yes. Messages are protected in transit. Encryption works regardless of mail server configurations and capabilities of the receiving server.
On servers? Yes. With most enterprise encryption products messages are encrypted when stored at the server, even if the receivers’ mail servers do not support encryption.
On Devices? No. The message is only encrypted when it leaves your device. Sent messages are typically stored without encryption in your sent mail folder. Received messages are decrypted when you open them and then saved decrypted in your inbox folder. The expectation for corporate devices is that they are protected using other methods such as Microsoft BitLocker to encrypt the data stored on the device. Unfortunately, if your recipients access your message on a home computer, they most likely will not have the TPM chip required to support BitLocker. They may not even have the Windows OS versions to support it. If your enterprise email encryption product allows accessing the message on smartphones, the messages saved there are almost never encrypted.
Lost or stolen mobile devices are the biggest cause of data breaches, including newsworthy breaches at NASA and Coca Cola. Skimping on your endpoint protection is not a good idea. Use disk encryption (Microsoft Windows BitLocker, or Mac OS X FileVault) or other data loss prevention products to protect the sensitive data stored on your devices. Blackberry, iOS and newer Android devices also support whole device encryption with a PIN. This article gives some more information on how to encrypt your device for some of the common operating systems.
Share this article on Facebook.
3. DIY Email Encryption
Yes, you can do it yourself! The basic concept here is that you create a public key and a private key. The public key, shared with the world, allows anyone to encrypt a message that they are sending you. The private key, known only to you, allows a decrypting of those messages. So if you are sending someone an encrypted message, your receiver will need a public and private key pair. You will also need to know their public key.
There is software available to do these things for you. Of course, you will need to set it up. They don’t call it DIY for nothing! Detailed instructions are available in this article for the fearless. Some products such as InfoCrypt, Enigmail, iSafeguard, Mailvelope, and SafeMess try to make the encryption steps easier. One of these, Mailvelope, is what the detailed DIY instructions use. But you still need to communicate the keys to your email recipients separately.
The big advantage here is that only you know the encryption keys. So no other organization, such as the National Security Agency (NSA) could read your email easily. There are laws that may prevent you from sending emails encrypted in this manner across international boundaries, so be aware.
Ease of Use: Difficult
Setup: Very hard. Who are we kidding, you need to set quite a few things up.
Daily Use: Difficult. Sending encrypted emails requires you to exchange a passphrase with your recipients, so they can open your messages. Except in the unlikely event they have also created a public and private key pair. And shared the public key with you previously over email.
Another thing users need to do on a regular basis is back up their public and private key pair. Somewhere away from your device, and preferably away from your home and office. This option requires users to personally keep that backup safe. After all, you do not want your secret key to be stolen or lost.
Easy For Clients To Receive: Difficult for most recipients, unless they happen to be DIY Email encryption enthusiasts. They will be required to obtain a passphrase from you. They may not be able to check the email in their preferred email app or webmail account, and may have to install new software.
Easy For Clients To Send: Forget about it!
| Ease of Use | Rating | Score |
|---|---|---|
| Setup | 1 | |
| Daily Use | 2 | |
| Client Receive | 1 | |
| Client Send | 0 | |
| Overall | 1 |

Security: High. Two of three aspects covered.
In Transit? Yes. No one other than you has your private key, so no one can read your message in transit (unless the encryption method is broken, which is not likely).
On Servers? Yes. Again, no one else has your keys.
On Devices? No. It is possible to configure your DIY solution to save your email encrypted, even in your sent mail folder. Of course, the keys are stored on the same device, and attackers know where the email programs save the keys. So it’s like leaving the key under the doormat at your front door. A little more secure than leaving the front door unlocked but the key is right there.

4. Secure Webmail
These look a lot like other webmail services such as Gmail, Yahoo! Mail or Hotmail, except that they support encryption. You sign up for one of these services and get a new email address just like you would get with any other webmail.
The big advantage here is that it is very easy to setup and start using. (A more up to date comparison with 2018 changes is available here
Options fall into two categories. First, programs that manage the keys for you, such as SendInc, safe-mail.net, and MDOfficeMail.com, among others. Some of the enterprise email encryption solutions, such as Rmail, also offer a webmail version.
Second, are programs that let you (or require you to) maintain your own encryption keys or passphrases. Such examples include Hushmail, LockBin, ProtonMail and Tutanota. The advantage is, like the DIY solutions, only you know your keys. Even the government cannot snoop on you. The difficulty is that you now need a way to exchange keys or passwords with recipients. Then you need to back up those keys somewhere safe and secret. This type of encryption email is not recommended for most businesses because it:
- may raise suspicion among your clients as to your reasons for avoiding government surveillance, and that does not foster trust
- introduces friction in your business transactions which is not good for growing your business.
So, the first type is what we evaluate here.
Ease of Use: Easy
Setup: Setup is almost as easy as signing up for a free webmail account except that these services are either not free or have restrictions in their free accounts and one needs to review those before choosing one.
- SendInc does offer a free account but the free account only saves your messages for 7 days and offers a limited 100MB storage quota, that will fill up quite fast with attachments.
- Safe-mail.net provides only 3MB of storage in the free account. Also, account creation is very slow. You submit the request along with a requested email alias for your @safe-mail.net address. They get back in a few days. Their website design appears quite dated and you should check if it will look good with your business branding, since clients will view your encrypted messages on the safe-mail.net website.
- MDOfficeMail.com does not have a free option. Their lowest cost tier, about $3/mo, includes 5GB of storage. You use an email address on their ‘MD’ friendly domains (such as yourname@mdofficemail.com) which may not be suitable for businesses other than physician offices.
- Encyro, though different from webmail in some regards, includes a free webmail-like account that allows sending to any email address with larger storage limits than either of the above options.
Daily use: Easy. Once you have an account, sending email is as easy as with other webmail services, except for HushMail. For HushMail, you need to select a password like question for every recipient - a question that only your recipient will be able to answer. This could be something less well known, such as their pet’s name or a password you share with them using a phone call or text message.
Easy for clients to receive: Reasonable Easy. Though details of what your client would need to do vary across services.
- SendInc requires the recipient to create a free SendInc account to read your message.
- Hushmail requires your recipient to answer a password-like question.
- Safe-mail is as easy as one click on a web link, with a captcha (manually entering a password displayed to your recipient). They do not require your client to create an account.
- Encyro is also as easy as one click on a web link. Captcha is only used in certain cases. Your client is not required to create an account to read the message.
Easy For Clients To Send: No. Encrypted webmail services do not allow your clients to send you an encrypted message unless they create their own account. (Encyro does allow your clients to send you secure messages or documents without creating an account, if you have a paid account.)
| Ease of Use | Rating | Score |
|---|---|---|
| Setup | 5 | |
| Daily Use | 5 | |
| Client Receive | 4 | |
| Client Send | 0 | |
| Overall | 3.5 |
Security: High. Two of three aspects covered
In Transit? Yes. Your message is always encrypted over the network, even if the recipient email server does not support encryption or is not configured for encryption.
On Servers? Yes. Encrypted webmail provides typically encrypt their storage as well.
On Device? No. Emails stay on your device sent folder or inbox without encryption.

5. Encyro
We did not place Encyro in the encrypted webmail category even though it is equally easy to set up, because of two significant differences.
-
Encyro allows your clients to send you encrypted messages or documents without having to sign up for any account. This is something that encrypted webmail, enterprise email encryption, or DIY email encryption do not allow.
-
Encyro does not store unencrypted messages on your device (smartphone, laptop, computer). They can be sent or received from mobile devices. Users can even forward attachments to others from their mobile device without downloading the attachment. However, messages and attachments are NOT stored in your email inbox or sent folder (unless you explicitly save something manually, or if the attachment was on your device before being emailed). This helps protect against device theft or loss.
The big advantage here is that the product was designed for business users without an IT department. It is not limited to compliance requirements. The design is geared from the ground up to provide the protection that businesses need. It also creates a smooth user experience that avoids added friction to your transactions.
Ease of use: Easy
Setup: Pretty much like webmail, you sign up for an account on the website. The sign up form does not require a credit card and defaults to a free account unless you opt to upgrade.
Daily Use: Easy. Much like webmail, you send encrypted messages from your Encyro account. No special encryption setup or option needs to be selected when sending a message.
Easy For Clients To Receive: Easy. Recipients do not need to create an account or password to view the message. One click takes them to the message. Like other encrypted webmail, messages links do expire to prevent unauthorized access.
Easy For Clients To Send: Yes. Your clients can send you encrypted messages or documents without signing up for an account. So you could email your client using the typical email address they already know. With that, ask them for some sensitive information with a secure reply link. Your link does not change, so you could even put it in your email signature. (Update: The upload page branding can now automatically match your business logo colors, using artificial intelligence, as shown here.)
| Ease of Use | Rating | Score |
|---|---|---|
| Setup | 5 | |
| Daily Use | 5 | |
| Client Receive | 5 | |
| Client Send | 5 | |
| Overall | 5 |
Security: Highest. All three of three aspects covered
In Transit? Yes. Your message is always encrypted over the network. Even if the recipient email server does not support encryption or is not configured for encryption.
On Servers? Yes. Your encrypted messages and documents stored encrypted and are backed up encrypted at multiple, physically separate locations. So you do not have to make your own copy, which could potentially invite a risk of data leak through device theft.
On Device? Yes. Encyro is probably the only solution that does not store the messages on your device in the inbox and sent mail folders. As a result, you have better protection against data leak in case of device theft. Bear in mind that device theft is the biggest cause of data leaks for all leaks reported by businesses and professionals, this is a huge advantage.
Ransomware: A further advantage with Encyro is protection from Ransomware. Ransomware is malicious software, similar to computer viruses, that prevents you from accessing your data stored on your own device, unless you pay the attacker a ransom. Since the attacker is typically located outside the US, local police departments have little authority or mechanisms to help. The FBI reports that ransomware incidents are rising rapidly. Recommendations to prevent ransomware attacks are available at this link published by the FBI’s Internet Crime Complaint Center (IC3). News reports from 2017 indicate that the crime is growing extremely fast, from $24 million in ransoms in 2015 to over a billion dollars in 2016. Of course, should most of your customer data be in the form of email, you could get to it from a different computer. Encyro keeps all your attachments securely encrypted and backed up. Yet, finding email attachments can be very difficult in the myriad email threads that get tangled over time. So Encyro offers a simple folder view with just the attachments organized by the contacts, without the message threads if you need to look for an attachment.
In Summary: Recommendations for Different Scenarios
To summarize the above discussion, here is the bottomline. The table below shows the scenarios for which the different types of email encryption are recommended. It also summarizes the ease of use and security scores from the above.
| Encryption Option | Security | Ease of Use | Salient Feature | Recommended For |
|---|---|---|---|---|
| Enterprise Email Encryption | 2/3 | 2/5 | Transparent for employees, easy to enforce policies |
|
| DIY Encryption | 2/3 | 1/5 | You control the keys, you trust no other organization |
|
| Secure webmail | 2/3 | 3.5/5 | Ease to setup, low cost |
|
| Encyro | 3/3 | 5/5 | Allows clients to send you encrypted messages or documents without creating an account, business friendly design, low cost |
|
| TLS | 1/3 | 5/5 | Happens behind the scenes, without you doing much |
|
Something of note in relation to the above table. If you are an independent professional or small business, and your clients are large corporations, it is worth checking if the same email encryption product as the corporate client can be used. This will make it easier for the corporate clients to communicate with you. But for most other businesses and professionals, the scores in the above table should help guide the choice.
Please share this article on Facebook now.

Appendix
This article did not cover a couple of other options that are sometimes used to prevent email data breaches. These are less relevant for professional and business email. We include them for completeness.
Self-destroying Email: SnapMail offers an email service for Gmail users where the email self-destructs 60s after it is opened by the recipient. This has limited use for business transactions.
Website Portals: Some websites implement their own document or message portal that customers sign into. Online banking websites and some hospitals use this. Dedicated industry workflow products such as Electronic Health Record (EHR) systems make it easier to set up such portals. However, this option is only available packaged with those larger solutions. It is not only expensive but also difficult to get customers to sign up for.